Illusory Truth Effect:
First, they covered the Illusory Truth Effect and how if people have seen information before then they tend to think it is accurate simply because they have been it before. For example, a statement that is repeated enough in the news tends to be perceived as true even though it is not. In Laura Galante’s TEDTalk, she talks about the illusory truth effect as the validity effect, truth effect, or reiteration effect. The more one hears the same news repeated over and over on TV, the Internet or on social media, the more likely the person is to believe that it is true.
Confirmation Bias:
Group three also talked about how confirmation bias is an individual’s inclination to try and understand evidence being presented as validation that their current belief or theories, regardless if it is accurate or not. With confirmation bias, once a person forms a view about something, they hold onto what they believe and look for information that confirms their view while ignoring contradictory information. A good example of when confirmation bias can be seen is peoples view on gun control. Whether a person is for or against gun control, they tend to search for and read the stories that support their belief or make interpretations of a story to support their views. Growing up I would hear, “oh, people hear what they want to hear” or “people are going to believe what they want to believe.” It was just a way of saying that people tend to interpret information in a way that confirms their beliefs about topics in the news. Confirmation bias can make people tune out others when they are not aligning with their beliefs or way of thinking. Interesting, the phrase, “Fake News” is circulating but maybe what is happening is that reporters and journalist are only researching and interviewing witnesses and experts that support and affirm their view so maybe we should be saying, “Confirmation Bias.”
Gatekeeping:
Next, the group talked about gatekeeping, which is the method of choosing, and then filtering, the content of media that is viewed within the time and space the person has available. A gatekeeper determines what information is allowed, and what is not allowed, to proceed past the "gate" to the people. Based on the preferences of the receiver the gatekeeper decides what information should reach them. The role of a gatekeeper is even more critical now since we have an abundance of ways to get news from TV, the Internet, and all kinds of social media platforms. There is a rise in outlets for which anyone can relay the news to the public. People are hearing breaking news before the information has even had time to be processed for truth and accuracy. Gatekeepers help bring out the truth and uphold professional standards. In a society where a significant portion of our news can come instantly from various social media platforms, the public needs a media gatekeeper that they can count on for accurate and credible information.
Agenda Setting:
Agenda setting is the ability of the media to impact what issues are viewed as important by the public and is considered to be a powerful influence that the media possesses. According to the presentation, agenda setting by the media can even go as far as to influence the focus of presidential campaigns. In 1972, the first examination was done in a study by McCombs and Shaw, who were researching the 1968 presidential campaigns and their primary emphasis was on awareness and information. The McCombs and Shaw study found that what the public saw as important issue for the 1968 US presidential election was what they were most feed from the media. As media has evolved so has the public’s relationship, need, trust and distrust of the media. The media plays a role in shaping politics by what they choose to put in the news and how much time they spend on that news. Through a multitude of ways, the media can shape the attention issue receive and of their importance. The media effects what people think about based on what they put in the news about our economy, society, politics and even science. Agenda setting by the media popularizes what issues become the focus of the public.
Overton Window:
The Overton Window is the range of views on different policies and agendas. These views change overtimes based on who is holding political office, social norms, and values. In 1990 in a conservative think tank in Michigan, Joseph Overton explained that public officials have to choose policies to campaign on that are politically acceptable during that time period. The window of opportunity will come and go depending on the economic and social tide. For example, at times thought radical and other times thought appropriate to discuss would be issues such as women voting, animal rights, climate change, immigration and Medicare for all.
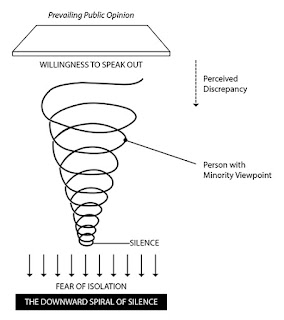
Spiral of Silence:
The Spiral of Silence, which was proposed by a German scientist, says that due to a person’s fear of being alone, they will not voice an opinion that goes against popular opinion of the group. The theory proposes that when it comes to public issues, individuals who think they have an opinion that is in the minority will stay silent, and those who think their opinion is in the majority will be more likely to discuss their opinion and the issue.